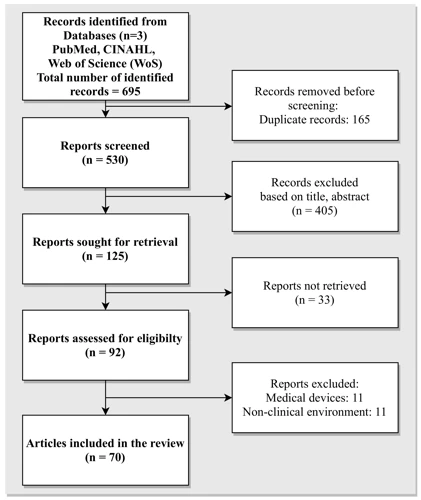
In the modern world, security is a top priority for both individuals and businesses. With the rise of technology, video security has become a popular solution for monitoring and protecting properties. However, video security is only one aspect of a comprehensive security strategy. In this blog post, we will explore the concept of “Beyond Video Security” and discuss the various components that make up a well-rounded security plan.
Physical Security

Physical security refers to the measures taken to protect people, property, and assets from physical harm or damage. This can include things like locks, gates, fences, and security personnel. In addition to video security, physical security is a crucial component of a comprehensive security strategy. By implementing a combination of both physical and video security measures, you can provide an additional layer of protection for your property and assets.
Cybersecurity

In today’s digital age, cybersecurity is becoming increasingly important. Cybersecurity refers to the practices and technologies used to protect computers, networks, and data from unauthorized access, use, disclosure, disruption, modification, or destruction. This includes things like firewalls, antivirus software, and encryption. By incorporating cybersecurity measures into your security plan, you can protect your digital assets and sensitive information from cyber threats.
Access Control

Access control is the process of regulating and managing who has access to certain areas or resources. This can include things like key cards, biometric scanners, and security guards. By implementing access control measures, you can ensure that only authorized individuals are able to enter certain areas, thus reducing the risk of theft, vandalism, and other security breaches.
Environmental Security
Environmental security refers to the measures taken to protect people, property, and assets from natural disasters and other environmental hazards. This can include things like fire suppression systems, emergency generators, and weather-resistant structures. By incorporating environmental security measures into your security plan, you can minimize the damage caused by natural disasters and other environmental hazards.
Incident Response

Incident response is the process of identifying, investigating, and mitigating security incidents. This can include things like data breaches, cyber attacks, and physical security breaches. By having an incident response plan in place, you can quickly and effectively respond to security incidents, thus minimizing the damage and preventing similar incidents from occurring in the future.
Training and Education
Training and education are essential components of a comprehensive security strategy. By educating employees and other stakeholders about security best practices and procedures, you can help to prevent security breaches and other incidents. Additionally, by providing regular training and updates, you can ensure that everyone is aware of the latest security threats and how to protect against them.
Policy and Compliance
Policy and compliance refer to the rules and regulations that govern security practices and procedures. This can include things like industry standards, government regulations, and company policies. By ensuring that your security practices and procedures are in compliance with relevant policies and regulations, you can help to prevent security breaches and other incidents, as well as avoid potential legal and financial penalties.
Continuity and Recovery
Continuity and recovery refer to the measures taken to ensure that your business can continue to operate in the event of a security incident or other disruption. This can include things like backup systems, disaster recovery plans, and business continuity plans. By having a continuity and recovery plan in place, you can minimize the impact of security incidents and other disruptions, and quickly get your business back up and running.
Monitoring and Analysis
Monitoring and analysis are essential components of a comprehensive security strategy. By continuously monitoring your security systems and analyzing the data, you can identify potential security threats and vulnerabilities, and take proactive steps to address them. Additionally, by analyzing security incident data, you can identify trends and patterns, and use that information to improve your security practices and procedures.
Looking to dive deeper into the world of video surveillance? Explore articles on costs of wireless video surveillance, NAS for video surveillance, importance of lighting in video surveillance, hidden costs of security vs video surveillance, and choosing cameras for video surveillance for a comprehensive understanding of the topic!
Conclusion
Video security is an important component of a comprehensive security strategy, but it is only one piece of the puzzle. By incorporating physical security, cybersecurity, access control, environmental security, incident response, training and education, policy and compliance, continuity and recovery, and monitoring and analysis into your security plan, you can provide a well-rounded, multi-layered approach to protecting your people, property, and assets.
In today’s world, security threats are constantly evolving, and it’s essential to stay one step ahead. By implementing a comprehensive security strategy that goes beyond video security, you can ensure that your property and assets are protected from a wide range of threats, and that you’re prepared to respond quickly and effectively to any security incidents that may occur.
In short, video security is important but it should be part of a more comprehensive security strategy that includes physical security, cybersecurity, access control, environmental security, incident response, training and education, policy and compliance, continuity and recovery, and monitoring and analysis. This will ensure that your property, people and assets are protected from a wide range of threats and you are prepared to respond quickly and effectively to any security incidents that may occur.







